
Every SaaS app needs permissions and RBAC. Why don't we have a standard developer API for authorization? Because authorization is a much harder architectural challenge than most other developer APIs.
APIs for billing, messaging, and authentication can be entirely SaaS based, but authorization is in the critical path of every application request. A viable solution has to be as lightweight as a library, returning results in milliseconds. At the same time, it needs to provide the control-plane benefits of cloud-based developer APIs.
It’s hard to believe that in 2022, every SaaS app still has to reinvent this wheel. We founded Aserto to fill this void and become the definitive developer API for authorization.
Today we’re opening our doors to any developer that wants to build permissions and RBAC correctly from the start. We also welcome teams that want to replace their existing home-grown solution with a rock-solid, secure-by-default authorization service that scales with their success.
Sign up now for your free account, or read below for more details.
The best of a library and a service
A solution that combines the best elements of a library and a service requires authorization to be done right next to the application, or as we say, “at the edge”. At the same time, it needs to centrally manage the artifacts used in authorization decisions. The Aserto authorizer is packaged as a docker container that you run as a sidecar or microservice in your environment. It syncs policies and user attributes from the control plane to the edge. It also forwards decision logs from the edge back to the control plane.
To make it easy to get started, we provide a hosted authorizer that supports the same APIs as the edge authorizer. That way, you can build your application without having to worry about standing up an edge authorizer.
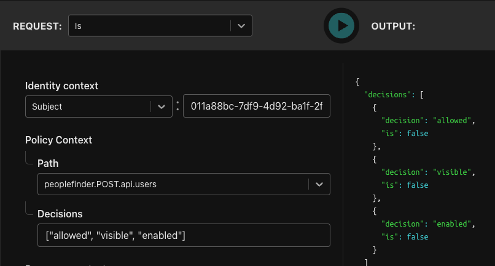
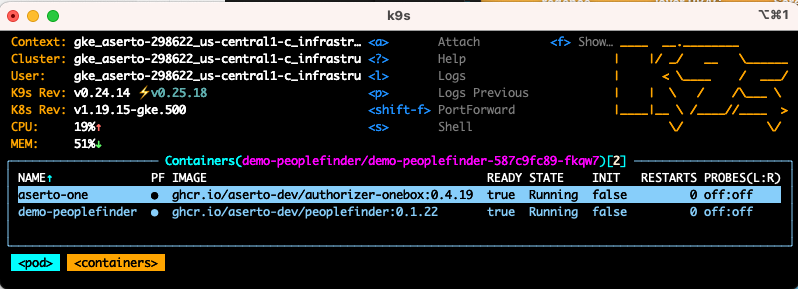
When it comes time to roll into production, you can deploy the edge authorizer as a sidecar running in the same pod as your application. Non-kubernetes shops can deploy it as a microservice in your VPC. In both cases, you get low-latency and high availability between your application and the edge authorizer.
Open-source at the core
We've worked on open source projects such as OpenStack, Cloud Foundry, and Kubernetes, so we know the power that comes from being part of an ecosystem. Aserto builds on the Open Policy Agent project, which passed its graduation milestone last year. OPA is used by infrastructure projects such as gatekeeper and conftest. The OPA community has grown to thousands of engineers across the world, and spans many technology companies.
Building on OPA means our customers use an open source engine and policy language that are already adopted across other use-cases. It also reduces vendor lock-in concerns, since customers can switch vendors or choose to build directly on the open source project.
Bringing the Docker workflow to the OPA ecosystem
OPA is a great engine, but its native packaging format for policies is a tarball. This means it lacks some of the critical elements of a modern packaging solution, such as image tagging, versioning, and signing. Aserto adopts the familiar "docker" workflow and brings these features to OPA policies.
Aserto builds on the shoulders of the Open Container Initiative (OCI) and Sigstore ecosystems. We’ve created the policy CLI and the Open Policy Registry as 100% open source tools that anyone can use, regardless of their OPA use-case.
Picks up where your IDP leaves off
The relationship between authentication and authorization is an important one. Aserto assumes that you have an identity provider that authenticates the user. Aserto picks up where your IDP leaves off, making the entire user context available to your authorization policy.
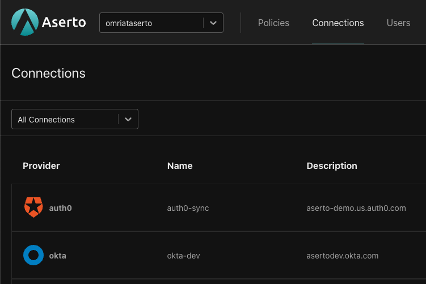
We allow you to sync your IDP(s) to Aserto’s directory, and automatically deliver any attribute changes from your IDP to the edge. The Aserto directory can also augment IDP attributes with roles and properties that are specific to your application.
No longer do you have to embed static permissions in an access token, which is insecure and clunky. Or make an HTTP call to your identity provider / directory in the critical path of the application request. Aserto caches the entire user context at the edge, giving your policies access to real-time data at low latency and 100% availability.
Aserto currently supports Auth0 and Okta out of the box, and our IDP plugin SDK makes it easy to add support for others, including your own custom IDP.
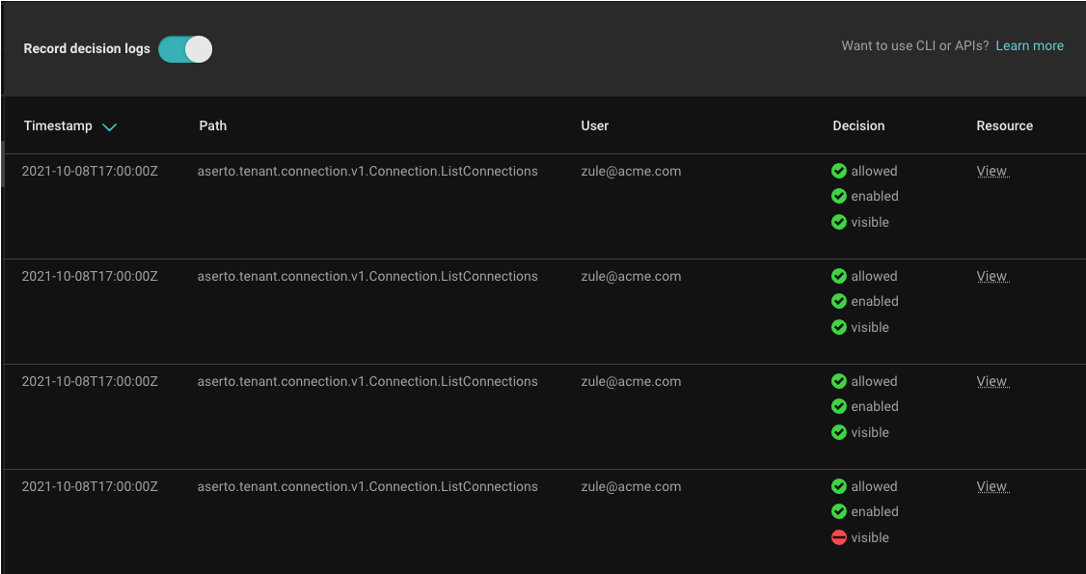
Enterprise-grade authorization requires complete audit trails
In enterprise-grade authorization systems, every decision needs to be explainable. Decision logs must include the policy, user attributes, and resource data that contributed to every decision. Aserto provides full audit trails for every authorization decision. It allows you to stream or download decision logs, and ingest them into your favorite log analytics system, such as ELK or Splunk.
Developer-centric solutions include batteries, but go to the metal
Last but not least, any developer API needs to be easy to learn and incorporate into your application. Aserto is contract-first, providing REST and gRPC APIs for down-to-the-metal developers. On top of these, we provide idiomatic SDKs for various languages and frameworks, including Express.js, React, Python, Flask, .NET, and Go. Whether you use our middleware or code to the APIs, Aserto is easy to integrate.

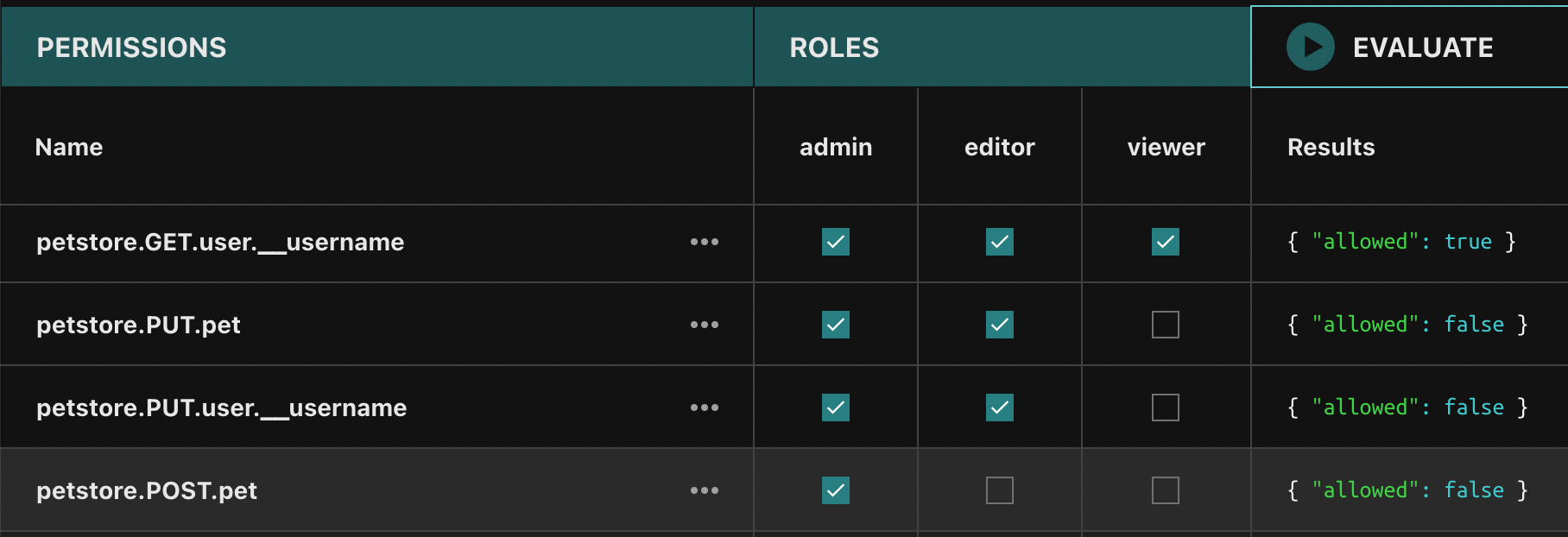
Just as importantly, the policy language needs to make the simple things easy, yet flexible enough to make any scenario possible. Rego is a general-purpose policy language, but brings with it a learning curve. We’ve defined common patterns for RBAC- and ABAC-style authorization policies, so you have a good starting point.
Finally, we have comprehensive documentation, quickstarts, samples, and executable API docs that make it easy to integrate Aserto into your application.
Get started today
To take Aserto out for a spin, sign up for a free account, or give our playground a whirl! Join our Slack community to get support and ask questions, and provide us with any feedback on how to make Aserto fit your use-case.
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)


