
Today, a breach is not a matter of if, but when. It happens to the biggest and best: USPS, LinkedIn, Equifax, are just a few examples. Once breached, determining the affected surface area is essential. Authorization decision logs are the easiest way to do that. They are also crucial for compliance and regulations, like HIPAA, SOC 2, and ISO 27001.
Authorization logs have additional applications and benefits. In this post, we review those benefits to demonstrate why authorization decision logs are important. We'll also share best practices around collecting and analyzing these logs to improve the application’s security posture, forensics, and auditability. Read on for the all the details.
What are authorization decision logs?
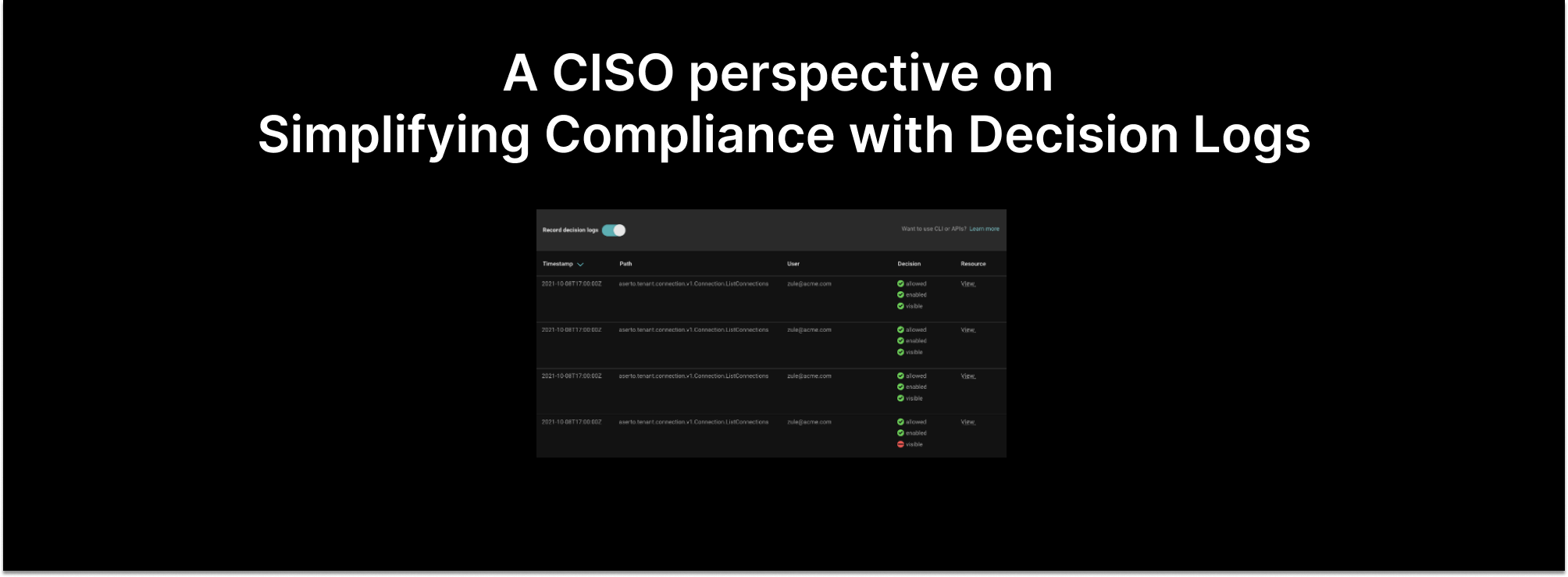
Authorization decision logs, or authorization audit logs, are similar in nature to other types of logs you might be familiar with, like application logs or authentication logs. They are records of every access decision made by the authorization system.
Authorization decision logs tend to include context relevant information required to make access decisions. The information captured in these logs are the inputs provided to the decision engine, along with the outcomes:
- Policy context; the policy and path to the rule that executed the decision, including the registry and repo where the policy is stored.
- User context, including the user ID.
- Resource context as provided by the application.
- Outcome: this differs by system, but most authorization services will provide some form of explanation of the outcome (i.e. why was this user declined access to that resource?). Aserto, for example, shares the names of the decisions paired with a boolean outcome for each to provide context around the decision.
Authentication vs authorization logs
Every authentication service provides authentication logs. These are records of successful and failed login attempts. Authentication logs focus on the login event, while authorization decision logs capture what happens after that event. They are complementary, and together they provide a comprehensive audit trail of user activity.
Authentication logs include detailed information about the device used to access the service, the user’s location, and other considerations that might influence risk. Generally, these logs only include information about the following events:
- Successful logins
- Login attempts
- Login errors
- Logouts, with additional information shows whether a logout was manual or due to session expiration.
This information can be useful to detect identity breaches. We can use authentication logs to identify brute force credential-guessing attempts, for example, as this will show up as failed authentications in the audit trail. They can pinpoint users that were affected by a breach, but not what those user accounts were able to access/do. That is where authorization audit logs come into play. Authorization decision logs will allow us to define the blast radius of the breach.
Authorization logs and compliance

Image by Freepik
Authorization decision logs enable us to provide legal evidence that the system is functioning in accordance with compliance requirements. These logs provide evidence that only authorized users were able to perform certain operations within the context of the application. This ability can be critical when we need to demonstrate we’ve met the requirements of regulatory frameworks, such as HIPAA, SOC 2, or ISO 27001.
Another side to authorization decision logs is the ability to provide clues that a breach has occurred. Analysis of the logs could show sudden spikes in declined authorizations for a user or set of users, which could indicate that their accounts have been compromised, and the attacker is probing additional systems that they can infiltrate. Since we might not see correlating spikes in failed logins for those users, without authorization audit logs, breaches could potentially go undetected for months if not longer.
Best practices for authorization decision logs
Best practices around authorization decision logs include automatically capturing these logs and aggregating them using a SIEM or log management system where they can be analyzed. Manual review of logs is error prone and inefficient.
There are a few ways we can set up a dedicated log viewer for authorization decision logs:
- Sending authorization decision logs to stdout: Most popular log aggregation tools such as Splunk and Elastic can collect logs written directly to the application’s standard output stream, if we use formats such as JSON with a consistent structure. This might not be an option, though, if we’re already sending application logs to stdout.
- Collecting logs with Logstash: Logstash is a data collector that is part of the Elastic suite. It can read logs from different sources, such as local files, events in a database, and requests sent to HTTP webhooks or websockets. Logstash ingests data from all those sources and forwards it to your preferred log aggregator.
- Viewing logs: Datadog and Grafana are two popular tools for aggregating, browsing and searching log data. Once the logs have been ingested, you can use these applications to query for events by properties, such as type and timespan.
Bonus: automatically capture every change to policy
Until now, we’ve focused on the logs of access decisions made by the authorization system. An audit trail of changes made to the underlying authorization logic is also useful for forensics and compliance.
Policy-as-code workflows get us half way there. We can externalize the authorization logic into a policy that is stored in its own repository, and utilize the git workflow for approval workflows and an audit trail of changes. Open policy containers is an open-source project that provides the ability to build authorization policies into immutable OCI images. This in turn enables us to version, sign, push and pull authorization policies as immutable images, and helps secure the software supply chain for these important artifacts.
Conclusion
Authorization decision logs might be one of the most undervalued aspects of externalized application authorization. They automatically capture a full audit trail of every action a user attempts to take in the application, and can be used to prove compliance with regulations and detect the affected surface area of a breach.
Authorization decision logs should be analyzed in tandem with authentication logs. Both sets of logs complement each other and taken together provide a full picture of a user’s journey from login to logout.
Aserto automatically captures authorization decision logs for every decision made. These logs can be easily streamed to your SIEM or logging system for further analysis, using pre-built integrations for Splunk and ELK. For more about Aserto decision logs, go here.
Our open-source authorizer, Topaz, also collects a record of every decision that you can download and share with your log aggregator for further analysis. You can integrate it with your app in just a few minutes to experience fine-grained authorization for yourself.
That’s it for now. As always, we’d love to hear from you! Drop us a line, or join our community Slack to engage with our developers directly.
Related Content

A CISO Perspective on Enterprise Forensics: How to Get Back From a Breach
Authorization decision logs provide accurate and detailed information about every action taken within the system for which those logs are being generated. These logs promote quick and effective responses which mitigate harm. And they do so more effectively than other logs or audit trails in isolation, and certainly when correlated with other information.
Mar 8th, 2023
A CISO Perspective on Simplifying Compliance with Decision Logs
Driving compliance, or managing risk, is key for any organization. Competent cybersecurity demands the centralization of authorization decision logs. Knowing who is accessing what, when and why is critical to safeguarding your assets and data. Learn more in this post.
Feb 7th, 2023
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)


