
With Identiverse and European Identity and Cloud conference (EIC) 2023 in the rearview mirror, it’s clear that modern authorization is gaining traction. A vibrant ecosystem of modern authorization vendors has emerged over the last few years and analyst firms, including Gartner and KuppingerCole, are covering the market and coining terms like Externalized Authorization and Policy-Based Access Management to describe this new wave of modern access control systems.
Ultimately, you can’t get to zero trust without fine-grained authorization. To effectively secure your business and limit the potential blast radius of a breach, fine-grained controls over what users can access are a must. Read on for all the details…
Identity-first security requires fine-grained authorization
The pandemic and the rise of remote work have acted as catalysts for a shift from the all too common network security approach most companies would rely on to an identity-based model. Add to that the fact that a whopping 84% of enterprises have suffered an identity breach this year, and it becomes clear why security professionals have shifted their focus from securing networks to securing identities.
An identity-first approach can protect users, apps, and data in ways that far exceed today's popular network security tools. Instead of setting up measures to secure every software, device, and resource, security professionals can invert the model by focusing on the most vulnerable assets in the organization - employee identities.
Embracing identity-first security also helps organizations adopt a zero trust approach to application security. Organizations can build fine-grained access controls around these identities. This way they aren’t just ensuring the right people have access, but that they have the right access.
Combining identity-first security with fine-grained authorization lets organizations adhere to the principles of least privilege and continuous verification which are both integral to zero trust. It also significantly reduces the potential damage of a breach. With fine-grained access controls you ensure that users' access is limited to what they need to perform their function at this moment. The identity and access are continuously verified upon every request, eliminating any standing permissions and overprovisioned roles.
Why now?
Identity is mostly a solved problem. Over the past 15 years, we’ve created standards and protocols, like OAuth2, OpenID Connect, and JWT that have created an interoperable identity fabric between systems. And there are companies like Auth0 and Okta that have brought developer tools to the market, so that today no one has to create a custom authentication / login experience.
But when it comes to access, it's an entirely different story. Today, every application is forced to reinvent the wheel and build their own authorization system. There are no standards, or protocols. It’s the wild west. So it only makes sense for modern authorization to be the next focus for Identity and Access Management professionals.
The two technical approaches to fine-grained authorization
Two ecosystems are emerging around modern authorization: policy-as-code and policy-as-data.
The policy-as-code camp is represented by Open Policy Agent (OPA), a CNCF graduated project. This approach focuses on decoupling policy from application code and into its own repo. Policies are sets of rules that are written in a declarative language and treated like any other code. Systems that use this approach typically offer attribute-based access control (ABAC) models, where access is determined based on user, resource, or environmental attributes.
The other approach is known as policy-as-data. This approach has gained popularity after Google published their paper on Zanzibar, the internal authorization system behind many Google applications, including Docs, Calendar, and Maps. This approach bases access decisions on application data. Policy-as-data systems typically use a relationship-based access control (ReBAC) model, where the relationships between subjects (users/groups) and objects (resources) determine access.
Both approaches have pros and cons. Policy-as-code is very flexible, but it requires developers to learn a domain specific language to get started and author policies. And in the case of OPA, you also need to build a data plane to get authorization data to the decision engine, as it does not offer that functionally out of the box.
In contrast, the authorization model described in the Zanzibar paper is very opinionated. The process of authorization is walking a graph of subjects, objects, and relationships and figuring out whether there was a set of edges on that graph that carries a permission. And it works for a surprising amount of use cases. But there are no standards, just a dozen open-source implementations of the Zanzibar paper, all providing a somewhat different interpretation.
Thankfully, you’re not married to just one approach. There are services out there that let you combine the best of both worlds. Topaz, an open-source authorization system, is one of those services. It supports both OPA policies and the Google Zanzibar data-centric model.
Where do vendors fall?
We know that the emerging modern authorization market is confusing. To try and simplify it and answer some of your most pressing questions we have analyzed a dozen modern authorization vendors across key dimensions, including the authorization models they support, their licensing model, and who they are built for.
Developer-centric or IT-centric
This classification answers the most basic question of “who is this for?” Is the vendor trying to sell to the entire organization and targeting IT as the buyer, or are they trying to sell into the application team and targeting the developers and technical leaders as the future users and implementers.
The dev-centric vendors can be classified further based on their level of sophistication. “Elvis” is a sophisticated developer, think of him as a C# developer. "Einstein" is the most sophisticated developer you can find, a C++ developer.
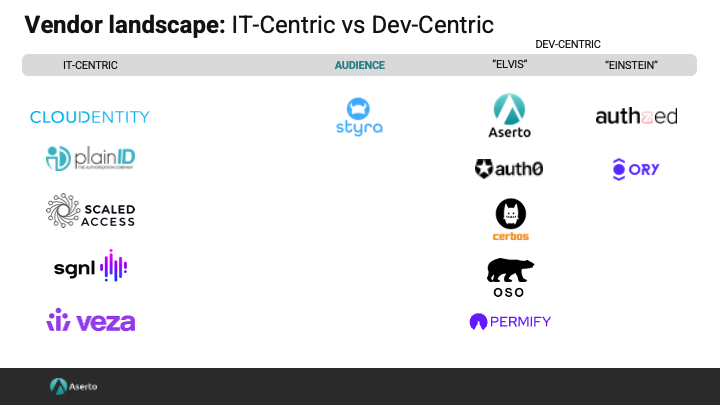
Vendors that build solutions for “Elvis” are trying to strike a balance between making the easy things simple, and the harder things possible. Their offerings have opinions, yet still provide enough flexibility to accommodate more complex use cases. And vendors that focus on “Einstein” build powerful toolkits for the most sophisticated developers.
Authorization model
One of the most important considerations is what authorization model/s does the vendor support, as this will determine how easily you can evolve your model as your needs change.
Here are the fine-grained authorization models that each vendor supports:
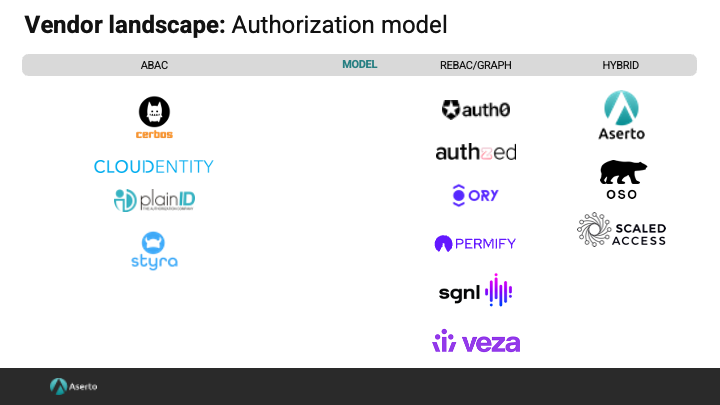
Each of the vendors reviewed support role-based models, with some providing multi-tenant RBAC out-of-the-box. When we look at finer-grained authorization models we see that ABAC-optimized offerings offer a policy language, and let you build policies that reason over user, resource, and environmental attributes. ReBAC vendors base access on the relationships between subjects (users/groups) and objects (resources). Vendors in this category offer graph-based directories and authorization systems. Finally, the vendors in the hybrid category combine approaches such as ABAC and ReBAC to deliver a flexible authorization model that brings the best of both.
Proprietary vs open-source
A vendor's license model is a key consideration for some organizations. Many vendors provide some open-source tooling, but does the vendor open-source their core assets?
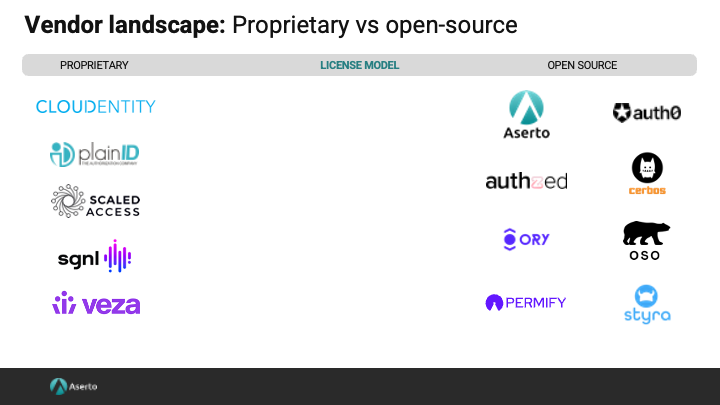
On the left you will see a list of vendors that may use open source in their solution, but have chosen not to open their core asset, their authorizer. On the right side, you have a set of vendors that have an open core model and have open-sourced their authorizers. In the middle are vendors with a significant open source asset (such as a control plane), but who have chosen to keep their core authorizer proprietary.
Conclusion
The future of IAM is fine-grained authorization. COVID and the rise of remote work have propelled identity-first security to center stage. But securing your identities will only get you so far. With 84% of enterprises reporting identity breaches this year alone, it is clear that we need to limit the blast area of a potential breach. And that is done through fine-grained controls over what users can access.
Identity is mostly a solved problem, access is far from that. It only makes sense that we unite as an industry and tackle the most difficult problem we face, namely how do we limit the potential damage of a breach. Because you know it’s not a matter of it, but when.
Related Content

Auth in everyday terms
“Auth” tends to be the term used to describe the process of Authentication and Authorization. But these are two distinct processes. Don't worry, even some experts make this mistake. In this post, we provide a real-world analogy that explains the differences between the two.
Aug 16th, 2023

Five open-source projects to secure access to your applications
Implementing user authentication and application authorization is hard. Thankfully, you don't have to do it all from scratch. Here are five open-source tools you can use to secure access to your applications and application resources.
Aug 23rd, 2023
Netflix authorizes extra members using environmental attributes
Netflix recently rolled out a system to combat account sharing, on a global scale. The enforcement system uses environmental attributes to determine access. This is a great real-world use-case for an attribute-based access control (ABAC) system. Get all the details in the post!
Sep 27th, 2023
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)


