
We had an amazing time at KubeCon last week. It was great to discuss cloud-native authorization and share the exciting news about the launch of Topaz, an open-source authorization system that combines the best of OPA and Google’s Zanzibar.
Up until now, there really wasn't a way to build fine-grained, policy-based, real-time access control for applications using open-source software. The open policy agent (OPA) is a great decision engine, but is optimized for infrastructure scenarios, like Kubernetes admission control. On the other hand, there is a new generation of access control popularized by Google's Zanzibar, the authorization system for Google Drive. This model is called relationship-based access control (ReBAC).
Topaz marries the two together to provide developers with the best of both worlds. Topaz is an OPA policy-based system with an embedded directory that allows you to answer questions like ”does user X have permission Y on object Z?” Bringing it all together and making it open-source is a real game changer.
As organizations grow and spin up more and more microservices, each one of these microservices does authorization differently. And, as a result, it's impossible to reason about the full surface area of permissions in the application. We are hearing from more and more organizations that they need a standard layer for authorization across the organization. That is what we are solving with Aserto.
Aserto is built on top of Topaz and provides a control plane which enables central management of policies, users, groups, objects, relations, and decision logs. And it syncs any changes to these with every locally-deployed authorizer over a real-time data fabric.
Industry leaders pathing the way
It seems that almost every industry leader has shared their story of how they built fine-grained authorization into their system. It's not just Google with Zanzibar, it's Intuit with AuthZ, it’s Airbnb with Himeji, it's Carta, and it's Netflix. All of them are now talking about how they extracted access control into its own service to manage complexity and regain agility.
These organizations have engineering powerhouses that are capable of building what every other organization can only dream of. And that is to have one access control service for all of their microservices, applications, and APIs.
Topaz is how the common organization is going to implement an access control service without having to build it in the same way that large companies with sizable engineering teams have.
More about this, the future of the cloud, and thoughts about WebAssembly in the video below:
Related Content

Announcing Topaz 0.30!
We're thrilled to announce Topaz 0.30! In the post we share all of the new features, including an upgraded modeling language with generalized support for subject-relations and intersections. A console that makes it easy to visualize and edit the policy, model, objects, and relationships. An evaluation environment and templates for simple RBAC, multi-tenant RBAC, Google Docs, and ABAC scenarios, to name a few.
Nov 6th, 2023

Announcing Topaz 0.31: our spiciest edition yet!
Get to know Topaz 0.31! We’ve expanded the ReBAC / Zanzibar-inspired modeling capabilities to support the full complement of operators: union, intersection, exclusion, and relation navigation (arrow operator). We’ve also added a set of templates which you can use to implement a few well-known examples of fine-grained authorization - Google Drive, Slack, and GitHub.
Feb 29th, 2024
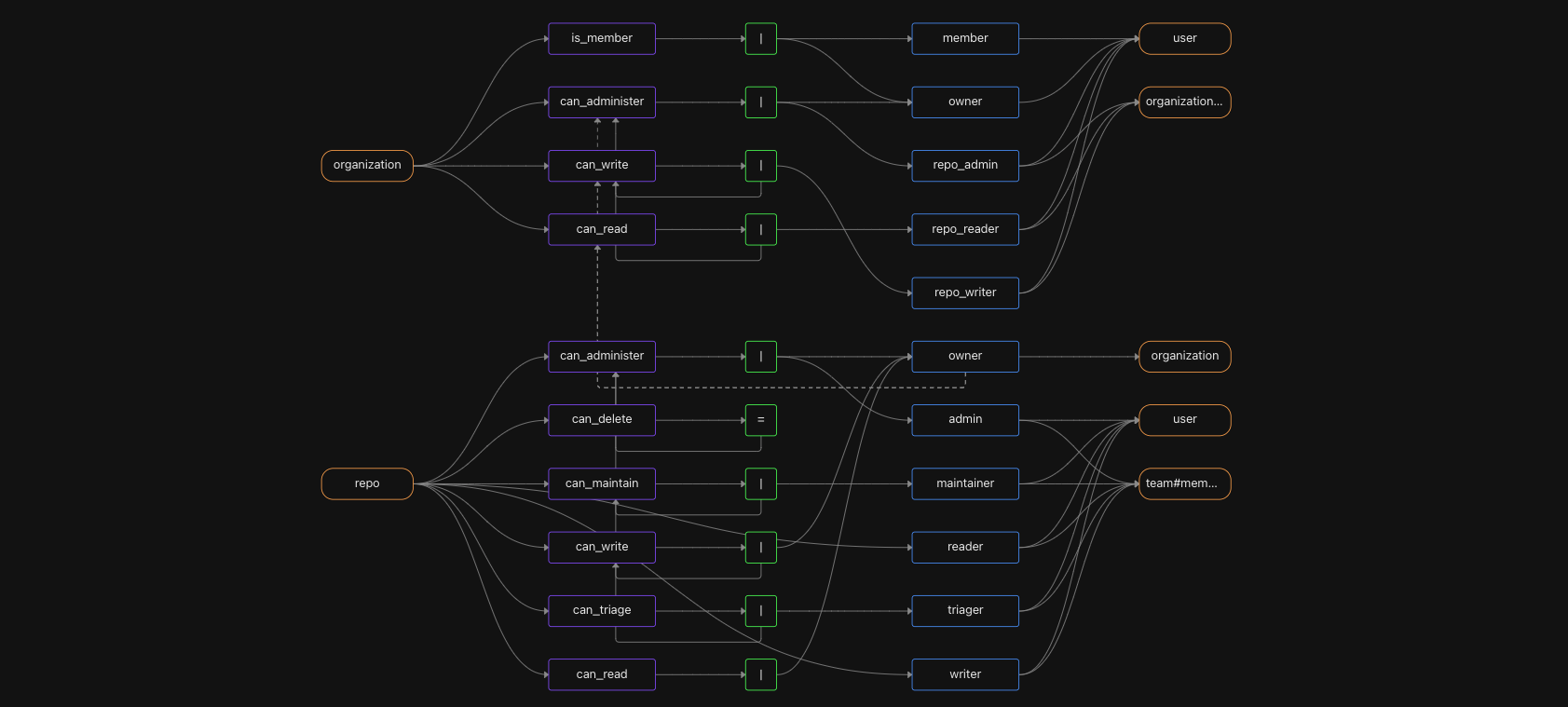
Authorize like GitHub: A real-world example of fine-grained authorization
GitHub is a familiar example of a sophisticated, fine-grained authorization model. GitHub's model includes roles, organization-wide permissions, and nested teams. Read on to learn how to model GitHub's permission system with Topaz.
Mar 21st, 2024
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)


