Fine-grained ABAC for cloud applications
Grant access based on dynamic attributes.
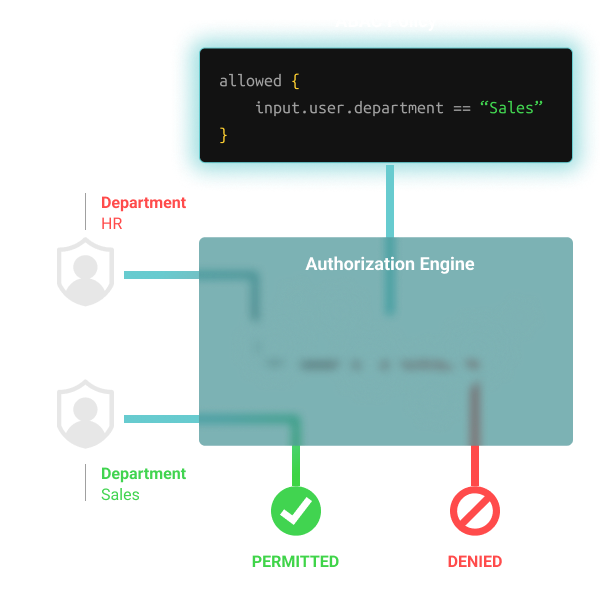



Fine-grained access based on user, resource & environmental attributes
Attribute-Based Access Control (ABAC) refers to the practice of making authorization decisions based on fine-grained attributes. With ABAC you can develop very specific, fine-grained rules that protect your organizational resources.
ABAC policies can be used to make authorization decisions that include user attributes such as department or office, resource attributes such as location, or environmental attributes such as day/time.

When roles aren't enough
Evolve your policy from RBAC to attribute-based access control to authorize based on user-centric attributes, resource attributes, and environmental attributes.

Real-time authorization
Attributes about users and resources are synced to the policy decision point in your cloud automatically and in real-time to eliminate the risk of access based on stale data. Enforce policy in milliseconds against the most up-to-date data.

Environment-based access
Influence both frontend behavior and backend logic based on where a user is logged in from, what region the application is running, or the day/time that an operation is invoked.

Manage policies in one place
Centrally manage policies and decision logs to simplify governance and compliance.

No lock-in
Built upon an open, cloud-native foundation, which includes Open Policy Agent (OPA), Topaz authorizer, Policy CLI, and many of the ideas in the Google Zanzibar system.

Explore popular authorization use cases

&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)