
KubeCon has always enjoyed a special place in my heart.
Back in 2015, I was running cloud engineering at HPE, and we were "all in" on the cloud-native movement. As Docker took the world by storm, we became founding members of the Linux Foundation's Open Container Project. And when Google launched Kubernetes and created the Cloud Native Computing Foundation, we pivoted our OSS strategy from OpenStack and Cloud Foundry to Docker and Kubernetes.
Later, when I became CPO of Puppet in 2017, I brought us into the CNCF and signed Puppet up to become one of the founding members of the Continuous Delivery Foundation.
In other words, I've always been a huge believer in the power and value of the cloud native ecosystem, and have attended nearly every KubeCon since the early days.
So far, infrastructure has been the focus for CNCF
In the Authorization space, the focus for the CNCF has been on authorizing access to the infrastructure. Graduated projects like Open Policy Agent and Kyverno mostly revolve around use-cases like Kubernetes admission control and RBAC.
This is only natural, since Kubernetes itself is a complex system, and evolution towards fine-grained access control is a long-term goal within the system.
We still see plenty of evidence for this. For example, the talk "Expanding the Capabilities of Kubernetes Access Control" by Lucas Kaldstrom (Upbound) and Jimmy Zelinskie (AuthZed) focused on how Kubernetes can become better at enforcing the principle of least privilege and reducing its attack surface area. Similarly, in their talk titled "Pushing Authorization Further", the SIG Auth members (Rita Zhang, Mo Khan, Jordan Liggett) talked about "RBAC++" inside of the Kubernetes API.
It's nice to see fine-grained authorization find its way into the underpinnings of Kubernetes... but that's only a small part of the story!
Application authorization is next
We're finally seeing signs that fine-grained authorization at the API and application layers are becoming top-of-mind for the cloud-native community.
For the first time, we saw at least six "pure-play" application authorization projects / companies (Aserto / Topaz, Cerbos, Oso, OpenFGA, Permit, SpiceDB) with some presence at KubeCon.
We all take different approaches to the problem, and are passionate about why our solutions excel. But one thing we don't argue about is that developers should externalize their application authorization to a purpose-built authorization system instead of building it themselves. Having more voices repeating the same message helps catalyze a movement.
Another anecdotal indication of the rise in the importance of cloud-native authorization is the sheer number of authorization talks I submitted that were accepted at this KubeCon - very much a record for me! 😀
I'll describe the three talks I gave below.
API Authorization
Traditionally, KubeCon has focused more on the DevOps persona than the developer. AppDeveloperCon is an official co-located event that is meant to fill this gap.
In my talk "Your Cheat Code for API Authorization", I covered the emerging practice of cloud-native authorization, and delved into its three important practices: fine-grained, policy-based, real-time access control.
Fine-grained authorization is typically enforced by the API / application code, but that isn't always practical, especially when a platform engineering team needs to consistently enforce access to APIs, and doesn't always control the code for every API.
To address this use-case, I showed how platform engineering teams can automate the process of onboarding services based on their OpenAPI spec, and enforce access control at the API Gateway.
Watch the full video:
Authorization Standards
I've written quite a bit about OpenID AuthZEN and why it matters. By creating a standard protocol for answering the question "does user U have permission P on resource R", we create a strong incentive for developers to follow this pattern, vendors to provide plug-compatible implementations, and engineering teams to give themselves the flexibility to get out of the business of "rolling their own" while avoiding locking themselves into a specific vendor's API.
In my talk "AuthZEN: The OpenID Connect of Authorization", I described exactly that. This talk was saved by 500 attendees into their schedule, and at least half of those folks were in the room for the talk.
The reaction was overwhelmingly positive: of the three dozen folks that surrounded me after the talk, there was palpable excitement about how big of a problem this is for cloud-native companies, and how necessary these standards are for them to sort through their authorization mess.
Watch the video below:
The Policy Engines Showdown
There are now a few popular open source authorization engines to choose from. Our friends at Permit put together a panel that brought together a number of these policy engines: CNCF's Open Policy Agent, AWS Cedar, Auth0's OpenFGA (which is also a CNCF sandbox project), and Aserto's very own Topaz.
This was a great opportunity for the authorization engines to explain what we do best, and how we compare on various attributes. We explored tradeoffs like policy-centricity vs data-centricity; statefulness vs statelessness; centralized vs distributed architectures; performance; and testing vs formal verification.
On these dimensions, Topaz is unique in that it brings the best of the two centers of gravity of the authorization world - "policy-as-code" (OPA) and "policy-as-data" (Zanzibar-oriented approaches).
- Topaz is both policy-centric (via the OPA engine) as well as data-centric (via its Zanzibar-style directory).
- While Topaz can be used as a stateless engine, it is strongly opinionated towards a stateful model, making it easy to store not just relationships, but also properties/attributes of objects and subjects. We like to say that Topaz is the missing data plane for OPA.
- By virtue of being distributed as a container image, Topaz can either be deployed as a sidecar (distributed architecture) or as a centralized microservice. In both cases, its control plane can keep policies and data in sync across deployments.
- Topaz is the fastest stateful authorizer on the market, typically delivering authorization decisions in under a millisecond.
- Topaz focuses on assertion suites as a way to test policies rather than formal verification methods. That is, we are more like OPA or OpenFGA than like Cedar.
Check out the full video below:
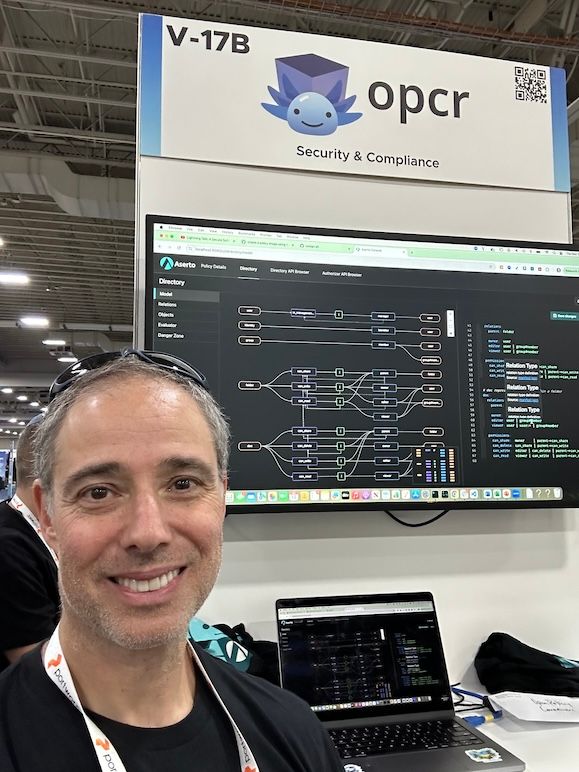
Open Policy Containers
Our own CNCF sandbox project, Open Policy Containers (OPCR), continues to draw interest from the community. OPCR is a "glue" project that brings together the OPA and OCI ecosystems by making it easy to package OPA policies as OCI images.
The policy CLI can be used just like docker - to build, tag, push, and pull policy images just like any docker image. This, in turn, allows DevOps teams to use tools like cosign to sign these images and verify their signatures, enabling a secure software supply chain for OPA policies.
I had a great time talking to a bunch of folks at the OPCR project kiosk. Engineers continue to struggle with the challenges of managing policies as important artifacts - whether for infrastructure scenarios or for application authorization. OPCR helps make it easier.
AuthZEN 1.0 on Techstrong
It's always fun connecting with the tech press at KubeCon, and my friend Alan Shimel from Techstrong was kind enough to interview me about the progress we've made at Aserto since last year, and about the AuthZEN 1.0 Implementers Draft which just got approved by the OpenID Foundation.
Looking to the future
It was gratifying to see so much attention on cloud-native authorization at this year's KubeCon. I can't wait until KubeCon + Cloud Native Con EU 2025 in London to see whether we can drive even more awareness around this topic!
Connect with us!
If you're looking for a great cloud-native authorization solution, go check out Topaz. Connect with us on our community slack, or set up a video call!
&color=rgb(100%2C100%2C100)&link=https%3A%2F%2Fgithub.com%2Faserto-dev%2Ftopaz)





